What is VAPT? A Complete Beginners Guide to Penetration Testing
A Vulnerability is basically a flaw in code that can be exploited to perform unauthorized actions. When exploited, can compromise the confidentiality, availability, and integrity of data stored in them.
Vulnerability Assessment:
It is the process of searching for security weaknesses or flaws in a network or server. The singular goal of a vulnerability assessment is to examine and detect, to ensure that no loophole would be overlooked.
Penetration Testing:
It is the process of exploring and exploiting flaws or vulnerabilities. This tactical approach checks if there is actually any real weakness within the system, network, or server. A penetration test, is either manual or automatic and being a form of ethical hacking, goes into a system or network and tries to hack it just to test the flaws.
What is Vulnerability Assessment and Penetration Testing?
VAPT combines both vulnerability assessment and penetration testing which seeks to identify defects within the security network, as well as to assess the intensity of it. VAPT also helps you understand the nature of the risk and recommends a course of action to help you take care of the vulnerabilities.
Reasons Behind Vulnerability of Systems
It’s important to understand that little acts of carelessness leaves systems vulnerable. The vulnerabilities are easily exploited by attackers to their advantages. So now, the question arises, what exactly makes a system vulnerable? There can be two reasons. Systems can become vulnerable due to errors in configuration and programming practices.
When it comes to networks, devices like routers, switches and servers, even firewalls and IPS systems often run with the default settings. Most of the time they are not configured at all and even if some changes are made they are found to be misconfigured.
To cite an example, firewalls come with a default user account named ‘admin’. The password, most of the time is also the same. Else the password set is extremely easy and guessable. So, if you do not make these necessary changes, the door always remains open for attackers to enter your system.
In case of errors in programming, entries made by users in a web application form are sent to a backend database server . The input is not parsed. Such cases can pave the way for SQL injection attacks or manipulation attacks.
What is Vulnerability Assessment?
Vulnerability assessment is a technical approach of scanning the entire system for security loopholes. It is done using certain tools and can also be done manually. At the end of the assessments all the vulnerabilities present in the system are listed out and classified according to the seriousness of damage they can cause.
Moreover, corrective measures are also suggested so that attackers do not find a way to exploit the loopholes and consequently compromise the system.
Vulnerability Assessment Process
Let’s have a look at the vulnerability assessment process explained in a step by step manner.
Goals and Objectives:
Specify your goals and objectives of vulnerability assessment.
Scope:
Define the scope of the task before Vulnerability assessment and testing.
There are three scopes and they are black box testing, white box testing and grey box testing.
Information Gathering:
Know the IT environment well by collecting information about it. Necessary information include IP address, version of operating system etc.
Vulnerability Detection:
The system is scanned by vulnerability scanners to detect the vulnerabilities.
Information Analysis and Planning:
The spotted loopholes will be analyzed to form a plan of penetrating the system or network.
What is Penetration Testing?
Penetration testing is a process to examine the existence of the vulnerability. It is a proof of concept approach. Further it needs to be proved that exploiting that loophole can cause damage to the system. Penetration testing is an intrusive approach and real damage can be caused to the system. Therefore, a lot of precautions are taken during the process. The following steps are included in the VAPT process:
- Application and network scanning
- Spotting security loopholes
- Exploiting the loopholes
- Compiling the test report.
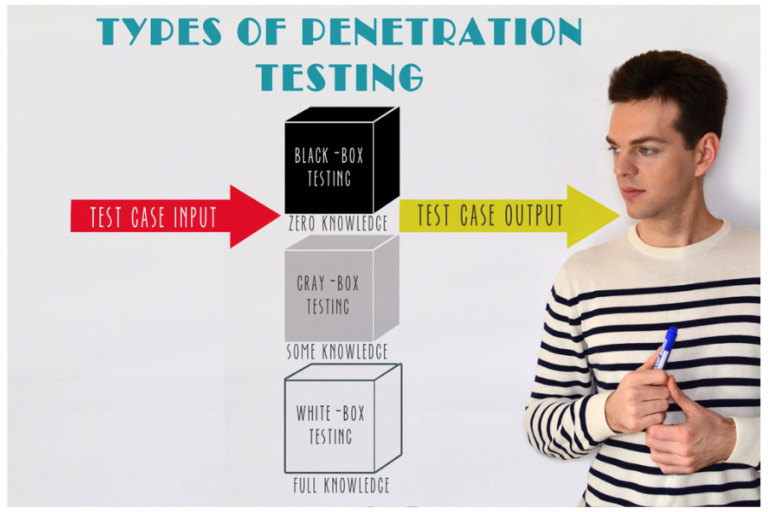
Types of Penetration Testing
Penetration testing is vital for every IT system to check the extent of vulnerability of the system and take steps with enough precautions to strengthen the security , so that it remains free from malicious attacks.
Penetration testing can be classified into three types.
White Box Testing:
You test within the internal network being completely aware about the internal network and system.
Black Box Testing:
You test from an external network without having any idea of the internal network or systems.
Gray Box Testing:
It’s a mixture of black and white box testing. Here, you can text from an internal or external network but you have the knowledge of the internal network.
Areas of Penetration Testing
Penetration Testing is a technical approach that ensures the security of the system by identifying the loopholes before an attacker does and taking the necessary corrective measures.
The different areas of penetration testing are:
- Application Penetration Testing
- Network Penetration Testing
- IOT Penetration Testing
- Cloud Penetration Testing
- Device Penetration Testing
- API Penetration Testing
Difference Between Vulnerability Assessment and Penetration Testing?
A vulnerability assessment is done to scan the system for security loopholes manually or using advanced tools. At the end corrective measures are provided. But the approach is not intrusive, so the operation of the system is not damaged.
In penetration testing, the vulnerabilities are spotted and steps are taken to overcome them. But here, the vulnerabilities are exploited in an authorized way. So the normal operation of the system can be damaged. This demands a lot of precautions.
Different VAPT Tools
As discussed, a lot of tools are available in the market to be used in the VAPT process. These are known as VAPT tools. But in reality most of them assist in VA. The penetration testing is generally done by the ethical hackers, manually. It is because PT is a process that demands great attention and there is always the fear of tools going haywire and giving out undesirable results without proper attention to the people using them.
So, it creates an illusion of the system’s security while it might not be really sure. This makes them susceptible to attacks at times. Still there are still some very effective tools which help in penetration testing. Given below are some of them.
- Nmap
- Acunetix
- Nessus
- OpenVAS
- Nexpose
- BurpSuite (PT)
- Metasploit (PT)
Importance of ‘False Positive’ and ‘False Negative’
Ethical hackers who deal with the above mentioned tools are very familiar with those two terms. The automated tools tend to display false positives and false negatives. A false positive is when there is no real vulnerability but one gets reported. In case of a false negative, there is a vulnerability, but even the tools skip it and fail to report. Both of them are harmful.
For a false positive result, a lot of time is wasted in locating it although it does not exist at all. For a false negative result, you know how dangerous it can be! The system remains vulnerable to attacks of malicious intent. This makes us give ‘automated tools’ a second thought, though we know nothing can be completely error free.
Importance of VAPT Testing and Training?
The increasing reliance on the internet has boosted the possibility of cyber crimes. Almost all the people, at present use some kind of web or mobile applications and it is certain that those carry some security loopholes which have escaped the grip of developers and security teams. These make the systems vulnerable. There are attackers out there, who would exploit these loopholes to get unauthorized access into your system. These malicious attacks can have severe consequences.
Attackers can steal or destroy sensitive information meant to be protected, they can extort money from you and can even compromise the whole system for their advantage. Organizations, when they fall prey to such attacks find it very difficult to make a comeback. This not only bares their confidential data but also affects the corporate revenues. Malicious attacks indicate that they did not stick to the security guidelines for which they pay huge amounts. It severely ruins their reputation.
This is enough to make you understand how important cyber security is. Therefore, several technical procedures have been devised to enhance the security of networks and systems. This article focuses on one such process, VAPT. This is carried out by ethical hackers to find out how vulnerable systems are, what are the security loopholes present, how they can be exploited by the attackers and corrective measures are suggested based on a systematic report that is compiled at the end of the process.
How to Become a Certified Penetration Tester?
Penetration Tester includes a curriculum that mixes certified ethical hacking, kali Linux, web vulnerability assessments and penetration testing. To become a professional Penetration Tester an individual should have hands-on experience with building a strong foundation for all information security practitioners.
To become a Certified Penetration Tester one should complete his CEH Certification 312-50 exam which lasts four hours, comprises 125 multiple-choice questions, and tests the candidates on the 20 areas of CEH curriculum.
After completion of CEH these are the extra 25 areas in which one has to be expertise in order to be a Certified Penetration Tester
Module 01 : Kali Linux operating system and its commands
Module 02 : Basics of Networking and its concepts
Module 03 : Penetration Testing and its Different methods
Module 04 : Exploit Testing and Penetration Attacking
Module 05 : Information Gathering, Reconnaissance, Scanning and Maintaining Accesses
Module 06 : Detection and Prevention of ARP, MITM Attacks
Module 07 : Analysing Client side and Server Side Attacks
Module 08 : How to perform and stop DoS / DDoS Attack
Module 09 : HTTP and HTTPS Protocol
Module 10 : OSINT Tools
Module 11 : File upload, Code Execution and File Inclusion
Module 12 : Broken Authentication and Session Management
Module 13 : Open and URL Redirection Concepts
Module 14 : No Rate Limitation and Parameter Tampering
Module 15 : HTML and Host Header Injections
Module 16 : Cross Site Scripting Findings and Exploitations
Module 17 : Insecure Cross Origin Resource Sharing
Module 18 : Top 10 OWASP Vulnerabilities
Module 19 : Practice and Setting up different labs
Module 20 : Practice on Vulnerable Applications and CTF
Module 21 : Mastering Burp Suite
Module 22 : Brute Force Web Applications
Module 23 : Firefox Security Add-ons
Module 24 : Importance of Documentation
Module 25 : Creating managerial, technical VAPT reports
Certified Penetration Tester Skills
Becoming a certified penetration tester requires strong technical skills. One should have a wide knowledge of the different methods of hacking which malicious hackers use in order to break into a system or a network. Extensive experience in the area of network security, web and mobile applications is must for Certified Penetration Tester.
Working experience in various Operating Systems like Windows, Unix, Linux, Parrot OS, iOS etc.., are mandatory. Good working knowledge of Microsoft and Linux servers, along with network switches and routers is required. A Certified Penetration Tester should be familiar with all the penetration testing softwares and tools.
Certified Penetration Tester Job Description
IT security is a growing field and Penetration Tester professionals play an important role in the IT field. The Penetration Testers mainly involve thwarting malicious hacking attempts through preventative counter-measures. Penetration Testers apply various techniques and use different penetration testing tools to compromise various systems.
Penetration Testers also use the same tools as malicious hackers in order to find vulnerabilities in the applications or systems or networks. This is an effective way to improve the cybersecurity of a business. As many business owners are becoming more aware of security risks, more penetration testers are being hired in order to ensure the protection of a company’s data.
As cyber attacks continue to increase throughout the world, the demand for Penetration Testers is also steadily increasing. Cyber Security requires the professionals with an ability to think outside the box to find new ways of entering a system illegally.
How Do I Get Started With Penetration Testing Training?
Interested in expanding your knowledge and advancing your skills on Ethical Hacking? Our teaching methodologies teach you valuable skills to detect potential defects and teach you to identify solutions to diverse security challenges.
We understand the importance of information data for any organization and also the drawbacks of the effect of data theft. With our excellent faculty we have designed a course in which our students can learn to safeguard assets. We offer certified and hands-on training and courses to enable you with all the essential skills required in the cyber security field.
We start from the basics and move to the more advanced tools and techniques. Through this course, students will come to understand major web application flaws and their exploitation.
Conclusion:
VAPT remains integral to the security of systems. Organizations must strictly adhere to it as this is probably the only way of managing risks. This procedure must be conducted at regular intervals. If your organization deals more with confidential data which has higher risk of getting leaked, then the process must be conducted frequently.
There are several tools available in the market which ease the process of finding the security loopholes and reporting them. But a crucial task like penetration testing is always done manually. Those who do it need to be highly experienced ethical hackers with a keen eye for vulnerabilities. This cannot be risked. We have seen how automated tools report spurious results at times. So they cannot be completely trusted to examine the security .
Hackers are often equipped with advanced skills and technologies and can often outwit ethical hackers. So the VAPT process needs to be done very meticulously and the techniques and tools used in the procedure need to be updated time to time. After all these, I hope it is clear to you that VAPT is the single most important tool used to safeguard the intellectual property of individuals and organizations.